This is part one of a multi-part blog post covering Amazon Web Services Identity and Access Management (IAM). IAM is an AWS service that enables customers to manage users and user permissions in AWS. The service is targeted at organizations with multiple users or systems that use Amazon EC2, AWS Management Console and other AWS services. IAM allows you to centrally manage users, security credentials, and permissions that control which AWS resources users can access.
AWS IAM Best Practices
AWS Root Account
It is a best practice to not use the AWS Root Account for your day-to-day administration tasks. Amazon recommends that the Root account be protected by a Multi Factor Authentication to provide an extra level of security around the most powerful account that AWS provides.
Create IAM Users
All users that are performing administration tasks in the console or that need access to AWS in general should have their own unique account for access to the AWS console.
Use Groups to Assign Permissions
AWS groups should contain users that correspond to their job functions and administrative responsibilities.
Grant Least Privilege
Working with IAM is a similar to working with Microsoft Active Directory Users and Groups. As many of us already know when planning Active Directory permissions we use the access principle of granting “least privilege”, and the same approach is recommended for AWS. The granting of least privilege access gives the user account only the privileges which are essential to perform that user's work. When planning access to AWS you must take into consideration that some users may not need full access to the AWS console. For example if you need to grant access to a user in your Accounting department to view the Billing information associated with your AWS account you would not want to grant that user administrator access to the console. We can use an AWS group and security policy to allow that user to log into the console and view the billing information.
Configure Strong Passwords
The password policy for your AWS account can be configured in the Password Policy section of the IAM console (see below). Most strong passwords contain at least 6 characters, one upper case and one lower case letter, one number and one special character. An example of a strong password that contains the previously mentioned password policy is “Sp@rkh0und”.
Enable MFA for Administrators
For extra security enable MFA for privileged IAM users (users who are allowed access to sensitive resources). With MFA, users have a device that generates a unique authentication code (a one-time password, or OTP) and users must provide both their user name, password and the OTP. AWS does not charge any additional fees for using MFA.
Use IAM Roles for Applications
Applications that run on an Amazon EC2 instance need credentials in order to access other AWS services. To provide credentials to the application in a secure way, use IAM roles. A role is an entity that has its own set of permissions, but that isn't a user or group. Roles also don't have their own permanent set of credentials the way IAM users do. Instead, a role is assumed by other entities. Credentials are then either associated with the assuming identity, or IAM dynamically provides temporary credentials (in the case of Amazon EC2).
Rotate Security Credentials
Require your users to change their passwords on a regular basis. Also rotate your administrators' access keys on a regular basis to ensure that these certificates are not compromised.
A comprehensive list of the AWS IAM Best Practices can be found here.
AWS IAM Console Overview
Log into your AWS account > Double click to launch IAM.
IAM Details Page
The IAM Details page provides a view of the current IAM features and current configurations.
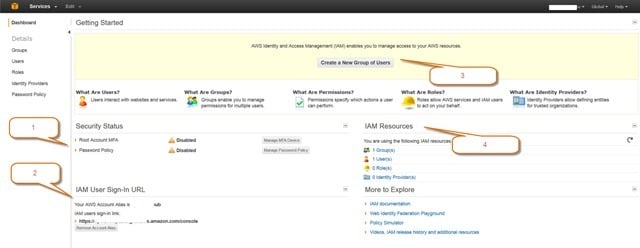
1. Security Status
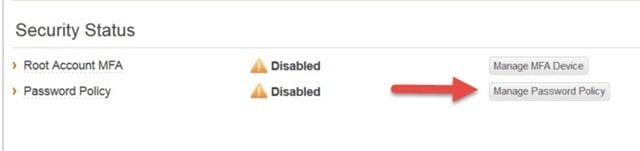
Root Account Multi Factor Authentication (MFA) - This button will allow you to configure a virtual or hardware based MFA device and will enforce the user logging in with the Root account to use the additional authentication. This ensures that Root access to the AWS account is fully secured. To activate you must install an AWS MFA-compatible application on the user’s Smartphone, PC or other device. You can find all of the AWS MFA-compatible applications here.
Password Policy – This is again similar to other familiar authentication protocols requiring the AWS user account passwords meet a certain standard, (password length, case requirements, numbers and special characters).
To configure the IAM Password, policy click on Manage Password Policy
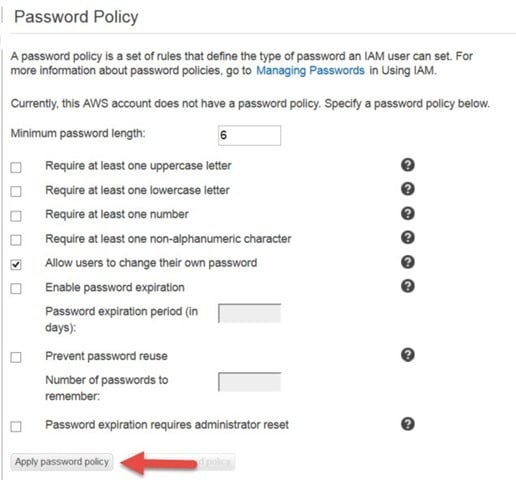
On the Password Policy page select the necessary components for your AWS password policy. Click Apply password policy when finished.
2 IAM User Sign-In URL
This is a very cool feature that allows the URL for your AWS account to be customized for your users to access the AWS console, (this URL must be unique in the AWS eco system).
3 Create IAM Groups
This button is a shortcut to the Groups page in the IAM console allowing for the quick creation of groups, the assignment of permissions and the addition of AWS users to the group.
4 IAM Resources
This also is a shortcut to views in the IAM Resource pages. Clicking on the IAM Resource link will take you to the associated page for Groups, Users, Roles and Identity providers in the AWS console. There are also many links to additional resources such as tutorials and services.
In part 2 of this post we will cover the Group features and administration in AWS Identity and Access Management.
Want to learn more about how Sparkhound can help with AWS? Check out this case study or reach out for more info today.
Information and material in our blog posts are provided "as is" with no warranties either expressed or implied. Each post is an individual expression of our Sparkies. Should you identify any such content that is harmful, malicious, sensitive or unnecessary, please contact marketing@sparkhound.com
Share this
You May Also Like
These Related Stories
SCDPM 2012 SQL Database Migration

Tip: Approve all In Progress Activities in Service Manager
